SETTING UP A SINGLE-NODE KUBERNETES CLUSTER ON AWS
KUBERNETES FUNDAMENTALS
Introduction
In this article, we’ll guide you through the process of installing and configuring a single-node Kubernetes cluster on AWS using CentOS-7 as the base operating system. We’ve divided the steps into five parts for clarity:
Series Overview
Part 1: Introduction and Pre-requisites
- Understand the purpose and benefits of setting up a Kubernetes cluster.
- Ensure you have the necessary pre-requisites, including an AWS account and a CentOS 7 base OS.
Part 2: Base OS Installation (CentOS 7)
- Install CentOS 7 on your chosen EC2 instance.
- Set up essential configurations and security settings.
Part 3: Installing and Configuring Docker Components
- Install Docker on your CentOS 7 instance.
- Configure Docker settings and ensure it’s running smoothly.
Part 4: Installing and Configuring Kubernetes Components
- Install Kubernetes components (such as kubeadm, kubelet, and kubectl) on your CentOS 7 instance.
- Configure Kubernetes settings and prepare for cluster setup.
Part 5: Creating and Deploying the Kubernetes Cluster
- Initialize the Kubernetes cluster using kubeadm.
- Verify that the master node is up and running.
- Add worker nodes to the cluster.
- Monitor the cluster and start deploying applications.
Whether you’re a DevOps engineer, system administrator, or developer, this guide equips you with the knowledge and practical steps needed to create your own Kubernetes environment on AWS.
LET’S DIVE INTO PART 1: INTRODUCTION AND PREREQUISITES!
SETTING UP A SINGLE-NODE KUBERNETES CLUSTER ON AWS
PART 1 – INTRODUCTION AND PREREQUISITES
INTRODUCTION
Kubernetes, often referred to as K8s, is an open-source system designed to automate the deployment, scaling, and management of containerized applications. Containers provide isolated runtime environments, bundling an application along with its dependencies, system libraries, binaries, and configuration files.
UNDERSTANDING SINGLE-NODE KUBERNETES CLUSTERS
A single-node Kubernetes cluster comprises two key components:
1. Master Node (Control Plane): Responsible for managing the overall cluster state, scheduling workloads, and maintaining configuration data.
2. Worker Node (Data Plane): Executes containers and hosts the actual application workloads.
Within Kubernetes, the smallest deployable unit is a pod, which can contain multiple containers functioning together as a microservice.
MANAGED KUBERNETES SOLUTIONS
Cloud providers offer managed Kubernetes services, such as AWS Elastic Kubernetes Service (EKS), Microsoft Azure Kubernetes Service (AKS), and Google Kubernetes Engine (GKE). With these services, you pay for control plane management while customizing data-plane resources (virtual machines) based on your application requirements.
ASSUMPTIONS AND ENVIRONMENT
For our deployment, we’ll make the following assumptions:
1. AWS Cloud Deployment:
- We’ll set up our Kubernetes cluster on AWS.
- You have a valid AWS account (including free tier accounts).
- We’ve chosen the AWS Asia Pacific (Mumbai) region (ap-south-1), but you can select any region.
2. Default VPC and Subnets:
- We’ll use the default VPC and subnets created during your account setup.
- Ensure that the subnet has internet gateway (IG) access.
3. Operating System:
- We’ll use Centos 7 as the OS for both master and worker nodes.
- Ubuntu Centos 7 supports 64-bit (x86) virtual machines.
4. Instance Types:
- OS Installation: t2.micro (1 vCPU + 1 GB RAM) – 1 instance
- Kubernetes Cluster: t3a.medium (2 vCPU + 4 GB RAM) – 2 instances
5. EBS Volume:
We’ll allocate a 10 GB io1 EBS volume.
6. User Setup:
We’ll create a dedicated user named “jenkins” for administering and monitoring the Kubernetes cluster.
Note that we won’t use the default “centos” user for security reasons.
Part 1
PREREQUISITES
Step 1: Configuring Key Pair
Follow these steps to create an SSH key pair for secure access to your EC2 instance:
1. Log in to AWS Console:
- Access your Amazon Web Services (AWS) console.
- Navigate to Services > EC2.
2. Create a New Key Pair:
- In the left tab, go to Network & Security > Key pairs.
- Click Create key pair.
- Provide the following details:
- Name: jenkins
- Key pair type: RSA
- Private key file format: .pem
- Tags:
- Key: Name
- Value: jenkins_ssh_key_pair
- Click Create key pair.
3. Download the Key:
- Download the key to your desktop/laptop as the file “jenkins.pem”.
- Note: This is a one-time download, so ensure it’s saved correctly as “jenkins.pem” or “jenkins.ppk” based on your platform.
4. System Platform Compatibility:
- Linux users: Use the .pem file format.
- Mac users: Use the .pem file format.
- Windows PowerShell users: Use the .pem file format.
- Windows PuTTY/Cygwin users: Use the .ppk file format.
5. Generating the Public Key:
- On your local computer, open a terminal or command prompt.
- Run the following commands:
$ chmod 700 "jenkins.pem" $ ssh-keygen -y -f "jenkins.pem"
- This generates a public key, which we’ll use when creating a new user for Docker/Kubernetes installation and configuration.
6. Keep the Public Key Secure:
- The generated public key (starting with “ssh-rsa”) is essential for secure access. Keep it safe and use it as needed.
Below is a screenshot of the Key pairs page.
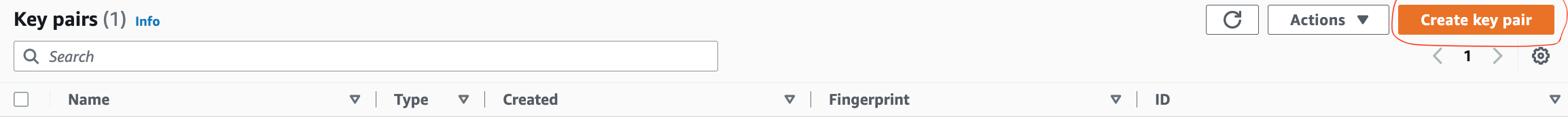

Step 2: Configuring Security Groups
By default, when you create an AWS account, a default security group is automatically generated. In this article, we’ll use this default security group for SSH access and Kubernetes-related activities.
Follow these steps to ensure SSH access to your EC2 instance:
1. Access the AWS Console:
- Log in to your Amazon Web Services (AWS) console.
- Navigate to Services > EC2.
2. Configure the Default Security Group:
- In the left tab, go to Network & Security > Security Groups.
- Click on the default security group.
- Go to the Inbound rules tab and click Edit inbound rules.
- Add the following rule:
- Type: SSH
- Protocol: TCP (defaults to this)
- Port: 22 (defaults to this)
- Source: 0.0.0.0/0 (allows connections from any IP)
- Description: Port for SSH (you can provide any name or value)
- Click Save rules.
3. Note on Security:
- While using 0.0.0.0/0 is acceptable for development and testing environments, it’s not recommended for production systems due to security risks.
Below is a screenshot of the security group with SSH port.
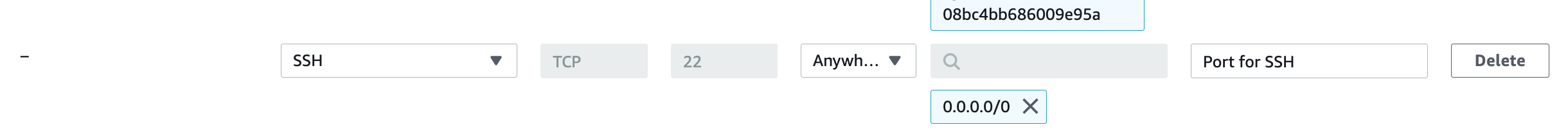

This completes the necessary prerequisites for your Kubernetes installation. In the next article, we’ll configure the CentOS 7 base OS, which will serve as the foundation for both master and worker nodes.
Part 2



Comments are closed.